BYOD is all the rage lately so it is imparative for us to be able to get it working properly. One environment that I found particularly challenging was getting Central Web Authentication working with FlexConnect and locally switched WLANs. In this article I will step through a working configuration from both the ISE (Identity Services Engine) and WLC (Wireless LAN Controller) perspectives.
NOTE: All components and configurations were performed in a lab environment. If you are working in a production environment be sure to validate the steps in your scenario.
We will cover the configuration requirements in two major sections: WLC Configuration and ISE Configuration
My lab consists of the following components:
• Cisco vWLC version 7.5 (beta)
• Cisco 1131 AG Access Point
• Cisco CSR1000v
• Cisco ISE version 1.1.2 in Stand Alone Mode
• ESXi 5.1
• Ubuntu Server for DNS, NTP, etc
• Catalyst 2950 Lab for basic connectivity
WLC Configuration
Here is a summary of the steps to be performed in this section:
1.Create the locally switched SSID
2.Create the access control list for Authenticated users
3.Create the access control list for web authentication redirect
4.Define the FlexConnect group
5.Configure the Access Point
1. Create new SSID named flex-guest
You can use any name you choose for your SSID. I chose one that I could use that would be easily identifiable in my lab. The SSID will be flex-guest in this example.

Once you have created the WLAN and are in the configuration details screen, set the L2 security to be None and Mac Filtering as shown below. This will allow ISE to treat this as wireless MAB (MAC Authentication Bypass) and it will flow through to the CWA profile to be created later.
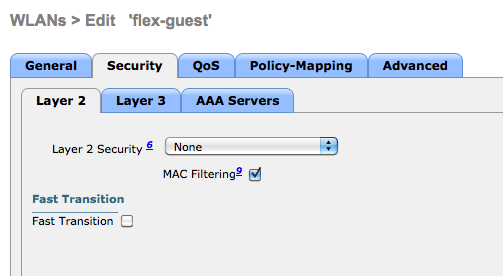
Make sure to select your RADIUS servers for authentication and accounting on the AAA Servers tab.

It is required to enable AAA Override and NAC State of “Radius NAC”.
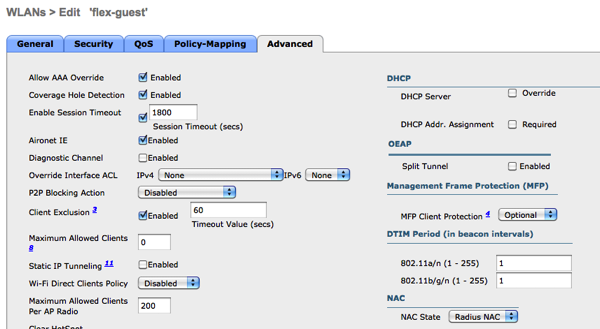
In the FlexConnect Section will will make this WLAN locally switched.

2. Create the flex-guest FlexConnect access control list
We will have to configure a couple of ACLs to be used in our solution. The first ACL will be the ACL that is applied to control what the guest users can do once authenticated. This will be referenced in our Authorization Policy by name.
The first ACL can be tailored to support your needs, but I have essentially allowed all traffic accept for ICMP to one of the IP addresses on the CSR1000v router for testing purposes.

3. Create the WEBAUTH-REDIRECT-ACL access-control list
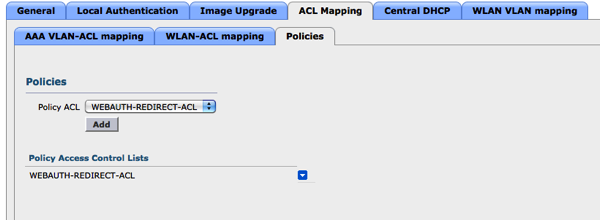
The WEBAUTH-REDIRECT-ACL is a FlexConnect ACL. The FlexConnect ACL is applied to the FlexConnect Group under the Policies tab later.
FlexConnect ACL

I created the ACL to be used during central web auth and will identify the traffic that will be let through without being redirected. There are some good examples out there in the Cisco trustsec docs you can copy. I basically allowed any traffic to / from the ISE box and also DNS to get us going.
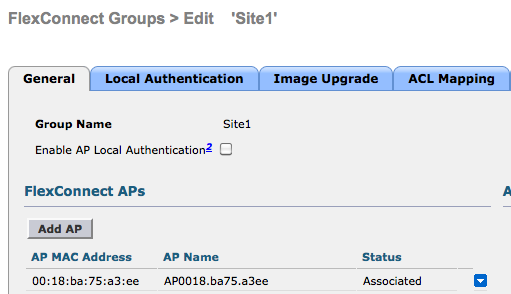
4. Define the FlexConnect Group
Create the Group and associate the access point.
Associate the WEBAUTH-REDIRECT-ACL under the ACL Mapping -> Policies tab.
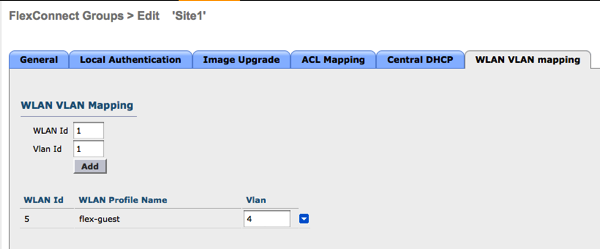
Add the WLAN to VLAN mapping
5. Configure the AP for FlexConnect
First, ensure the access point is in AP Mode FlexConnect

Enable VLAN Support on the FlexConnect Tab.
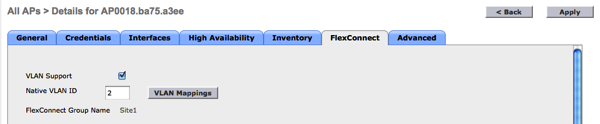
Click the VLAN Mappings Tab and add the VLAN to the AP.
Then at the bottom you will associated the FlexConnect FLEX-GUEST ACL created earlier.

ISE Related Configurations
The assumption will be that you have a basic, functional ISE installation. I will talk about only the specific configurations related to the FlexConnect lab I am working on.
1.Guest Account Created and Active
2.Result Element Create for CWA
3.Result Element Created for FLEX-GUEST
4.AuthZ Policy created for CWA
5.AuthZ Policy create for Activated Guest
1. Guest Account Creation
Login into your sponsor portal (default https://ise:8443) and create a guest account to be used during testing
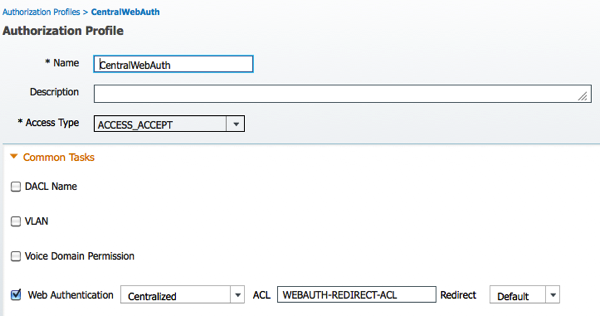
2. Create the Result Policy Element for central web auth

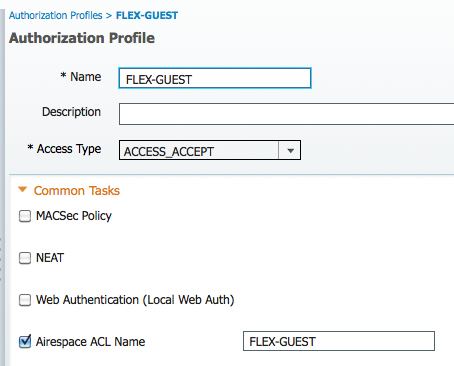
3. Create the Result Policy Element for FLEX-GUEST
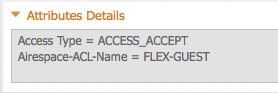
4. Create the AuthZ policy for CWA
I am using the default catch all authorization policy in this example and have associated it with the result, CentralWebAuth, created in a prior step.
5. Create the AuthZ policy for FLEX-GUEST
This rules is using the ActivatedGuest endpoint group for guests and the result of FLEX-GUEST.
The basic flow will be:
1.Client Connects to the flex-guest SSID
2.WLC will send the RADIUS packet to ISE as MAB
3.Since there is not an endpoint with the MAC address in the database we will allow authentication to “Continue” through to Authorization.
4.There will also not be a match in the Authorization rules yet so it will end up at the default rule (CWA policy from above)
5.ISE returns RADIUS packet with the ACL name for webauth-redirect to be used and access-accept
6.WLC will use the webauth redirect ACL created locally to determine what traffic will qualify for redirect and send browser traffic to the ISE guest portal
7.User will enter the guest username and password created in the sponsor portal
8.Following success authentication the COA is issued and the ACL from (FLEX-GUEST) will replace the webauth redirect and the client will enter the run state.